Hide User from Login Page - Special Accounts
To hide this account the steps are fairly straightforward but it is important to note that you need to be logged in as a local admin to pull this off.
-
Load up Registry Editor (regedit) and navigate to the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon -
From here create two new keys nested under Winlogon:
- SpecialAccounts
- UserList
- SpecialAccounts
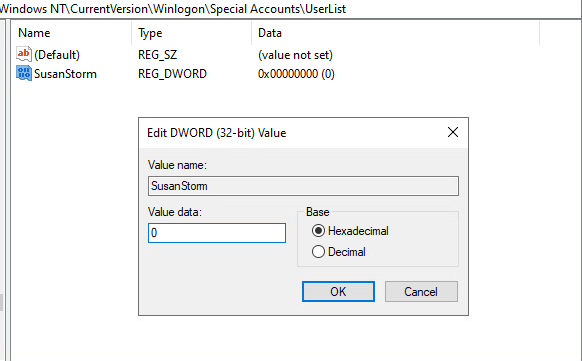
- Create a new DWORD value under the newly created
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlistkey
- Name that value the same name as the account you need to hide and set the value to
0. Changing this value to1would make the account visible again.
Invisible Artifacts
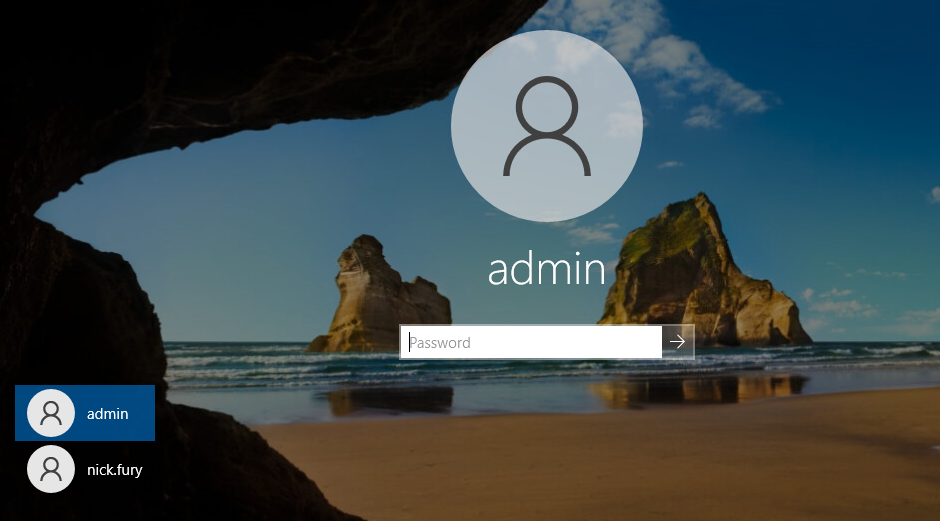
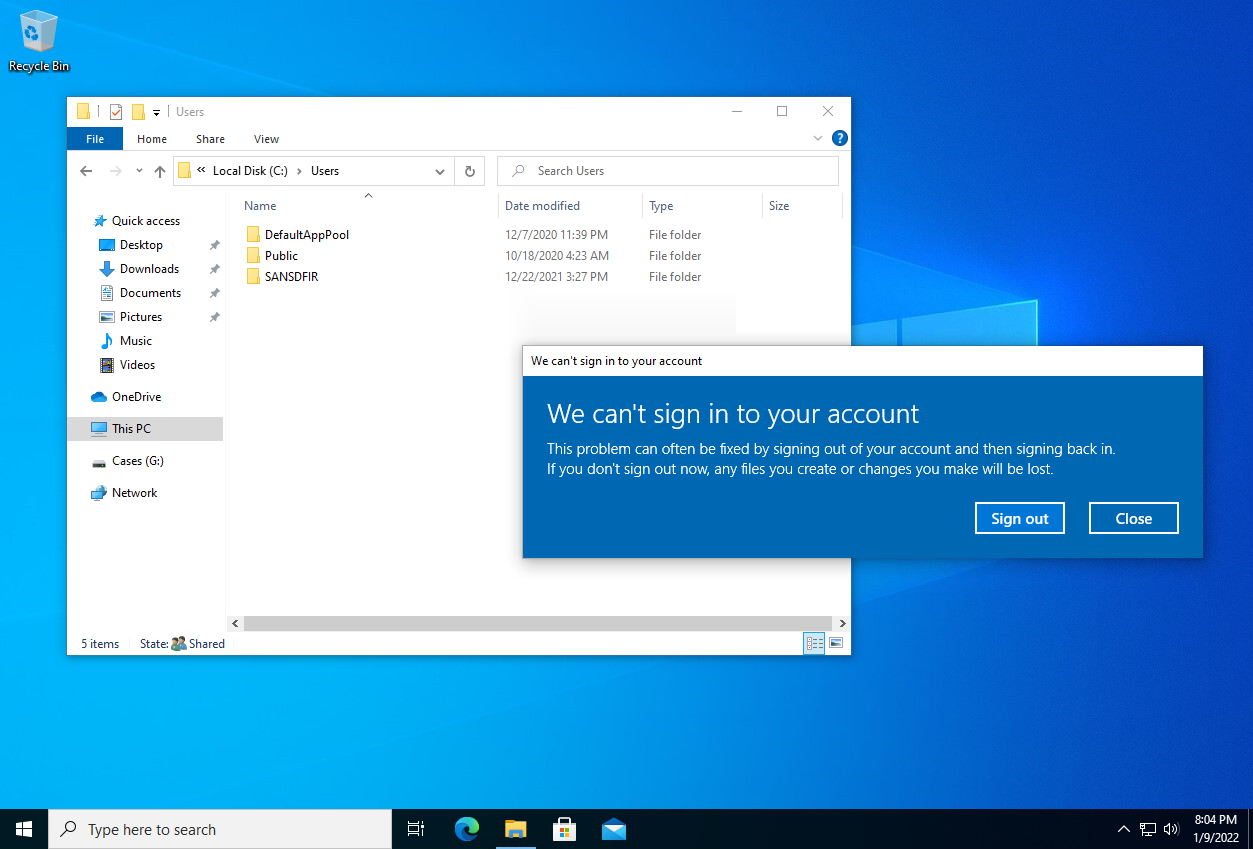
The change should take place immediately, but you can log out of your account and the hidden account should not appear on the list of available users.
I was under the impression that the login page was the only place that would be affected but as I was switching users, I noticed that SusanStorm was missing from the user list on the Start Menu too. This got me curious about where else she had become invisible.
Visible Artifacts
The next thing I wanted to know was where you COULD find evidence of SusanStorm
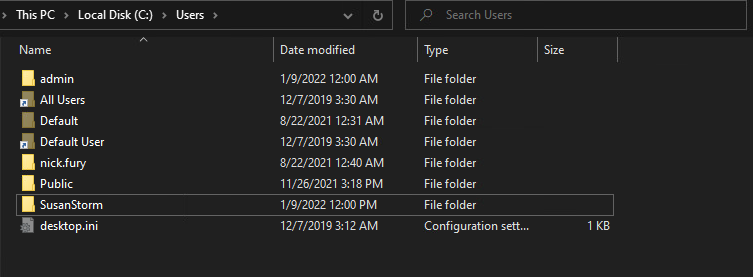
Home Directory
- The registry change did nothing to the visibility of the user directory for the account, which didn’t surprise me as NTFS doesn’t offer a way for a file to be more than “hidden” as far as I know.
What I did learn during this research was that a home directory is not actually required for users.
- If the user has not yet logged into the machine, a user home directory hasn’t been created yet.
- Manually deleting the SusanStorm home directory caused an error when I logged back in but it still took me to a working desktop logged in as SusanStorm. More research would be required to learn if there were any limitations to this account.
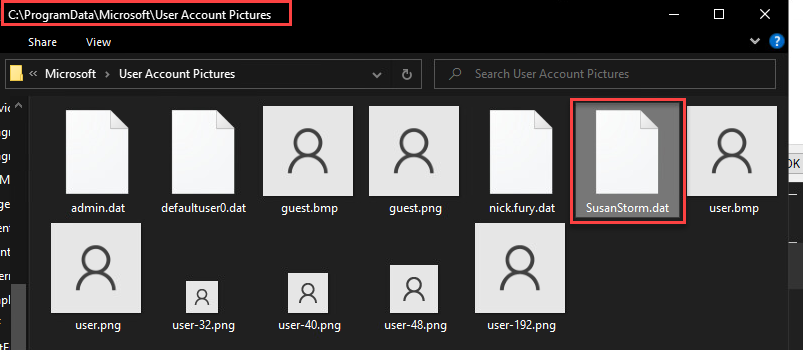
User Account Pictures
There is also evidence under C:\ProgramData\Microsoft\User Account Pictures. This artifact may be one that attackers overlook even after they delete a hidden user’s home directory. Interestingly enough, this artifact persisted after I had removed her account.
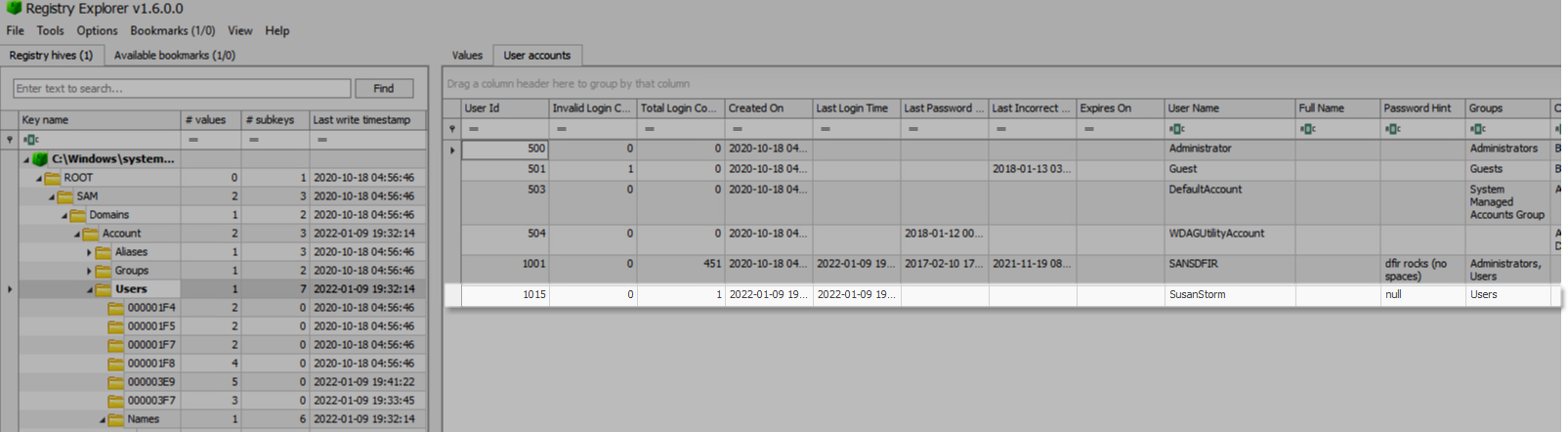
SAM Registry
Windows keeps most things straight and in order using registry files so I wasn’t too surprised when I found evidence of the account in the SAM hive. (SAM\Domains\Account\Users\) Because the hidden state is something that can be turned on and off, Windows doesn’t remove any of the critical pieces of data required to maintain and store this account. This is just one example of where I found evidence in the Registry but am sure that you could uncover this account in countless registry locations.